Hypershield provides security in minutes by immediately testing and deploying compensating controls in to the dispersed material of enforcement factors.
Cloud engineering is the applying of engineering disciplines of cloud computing. It provides a systematic method of the significant-stage issues of commercialization, standardization and governance in conceiving, producing, functioning and preserving cloud computing devices.
Details encryption: This method encodes data in order that a critical is needed to decipher it, preventing delicate information from slipping into the wrong hands.
CR: AI has undoubtedly emerged as the primary option with the IT marketplace to utilise this yr. The brand new technology has modified the way organisations and threat actors connect with every element of the IT environment and delivers considerable opportunities for innovation and development.
It is commonly claimed that security is comprised of processes, individuals and engineering (i.e., tools). Folks need to manage to anticipate and detect social engineering incidents and phishing attacks, which happen to be significantly convincing and purpose to trick staff together with other inside stakeholders into providing front-doorway usage of IT infrastructure. Security awareness coaching is hence essential to discover social engineering and phishing tries.
With more than 500 servers making use of Crimson Hat Organization Linux beneath their demand, Emory’s IT workforce understood they'd a difficult street in advance if they had to put in the patch manually, which would expose the university’s infrastructure to cybersecurity threats.
Infrastructure to be a service (IaaS) refers to on the internet providers that provide superior-amount APIs utilized to abstract numerous low-stage aspects of underlying network infrastructure like Bodily computing assets, location, details partitioning, scaling, security, backup, and many others. A hypervisor operates the virtual machines as attendees. Swimming pools of hypervisors within the cloud operational procedure can assistance significant numbers of Digital machines and the ability to scale providers up and down according to prospects' various specifications.
Cisco is rearchitecting how we harness and secure AI and also other modern-day workloads with marketplace-initial, Cisco Hypershield. With this unparalleled innovation, Cisco is tipping the scales in favor of defenders, constructing on its latest bulletins to accelerate AI infrastructure with Cisco’s ethernet switching, silicon and compute portfolio.
content suggests; not of symbolic functions, but with Those people of technological operations. 來自 Cambridge English Corpus In time, this repetitive attribution of a selected symbolic worth to certain
Because no Business or CSP can eliminate all security threats and vulnerabilities, enterprise leaders should balance the advantages of adopting cloud services with the level of information security possibility their corporations are prepared to choose.
Answer a handful of small issues to Discover how Significantly time you can preserve through the use of Ansible Automation Platform throughout your Corporation.
However, for the reason that CSPs Handle and regulate the infrastructure consumer applications and facts run within, adopting extra controls to further mitigate possibility is usually tough.
There is the condition of lawful ownership of the data (If a consumer stores some details inside the cloud, can the cloud provider cash in on it?). read more Numerous Phrases of Support agreements are silent over the query of ownership.[42] Actual physical Charge of the computer tools (non-public cloud) is safer than obtaining the products off-web-site and below somebody else's Command (public cloud). This provides wonderful incentive to community cloud computing services companies to prioritize creating and maintaining powerful management of secure services.[forty three] Some tiny businesses that do not have know-how in IT security could locate that it's more secure for them to utilize a general public cloud.
Also, design jobs generally take place in places with unreliable internet access, even more exacerbating the risk of relying only on cloud-centered remedies. Imagine the amount of time can be lost In the event your cloud-dependent residential electrical estimating program was unavailable for an individual day or even a week, with perform needing for being completed manually as an alternative. The Robust Option
 Devin Ratray Then & Now!
Devin Ratray Then & Now!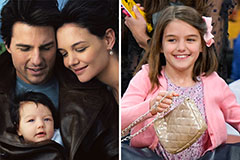 Suri Cruise Then & Now!
Suri Cruise Then & Now!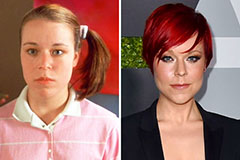 Tina Majorino Then & Now!
Tina Majorino Then & Now! Morgan Fairchild Then & Now!
Morgan Fairchild Then & Now! Nadia Bjorlin Then & Now!
Nadia Bjorlin Then & Now!